Cybersecurity monitoring and event evaluation – Video course
Learn what the cybersecurity monitoring process contains under the framework of continual cybersecurity activities and ISO/SAE 21434 requirements. Moreover, you will learn the role of cybersecurity information and triage for cybersecurity monitoring. As a further step, you will also learn about event evaluation and get a practical example.
Understand the role of cybersecurity monitoring and event evaluation in continual cybersecurity activities and ISO/SAE 21434 requirements
Continual cybersecurity activities are required to monitor threats or vulnerabilities and manage them. In this video course, we will focus on the first two activities: Cybersecurity Monitoring and Event Evaluation.
First, we will highlight the importance and role of cybersecurity monitoring in the context of continual cybersecurity activities. Then, we will define what cybersecurity monitoring is according to ISO/SAE 21434. In doing so, we will shortly introduce the role of triage in cybersecurity monitoring.
Once cybersecurity monitoring is defined, we will go deeper into explaining what it consists of and how it can be configured. Moreover, we will define what threat intelligence is and what are some best practices, including sharing practices between vehicle cybersecurity and enterprise cybersecurity. Here, we will also briefly introduce the ISO/SAE 21434 requirement for the collection of cybersecurity information.
As a follow up, we will define what cybersecurity information is and from which external and internal sources it can be gathered. Next, we will also provide some criteria to prioritize information about threats. Furthermore, we will also present what the benefits of a good cybersecurity monitoring infrastructure are.
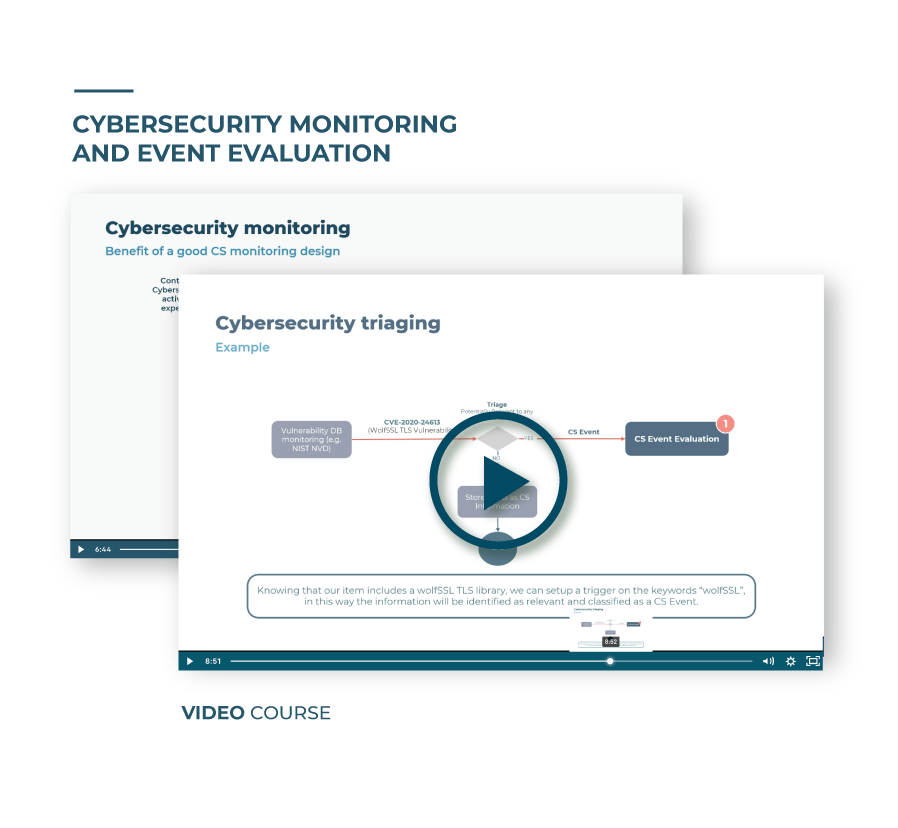
After you understand how cybersecurity monitoring prescreens cybersecurity information, we will explain how cybersecurity triage evaluates relevance and determines a cybersecurity event. To illustrate this concept, we will go over a practical cybersecurity triage example.
Finally, we will explain how the next step in cybersecurity continual activities, cybersecurity event evaluation, looks like and define it as per ISO/SAE 21434.
Who the „Cybersecurity monitoring and event evaluation“ video course is made for
All professionals in the organization
Because cybersecurity information can be gathered from multiple sources, it is helpful when everyone in the organization is aware of its availability to support cybersecurity monitoring. Moreover, in this video course, you will get to know how vehicle cybersecurity shares common practices with enterprise cybersecurity.
Professionals involved in automotive cybersecurity
Applying a good cybersecurity monitoring design not only helps identifying new threats and handling them right, but it is also related to reduced expenses on continuous cybersecurity activities. Therefore it is on everyone’s best interest to know what a good cybersecurity monitoring design requires and how it can ensure ISO/SAE 21434 compliance.
Product Security Incident Response Team (PSIRT) Overview video course content
Before we begin with the learning material, we will go over the learning objectives and importance of this video course.
II. Introduction to Cybersecurity monitoring and event evaluation
Recognize where the cybersecurity monitoring and event evaluation take in place in the overall continual cybersecurity activities and how they are defined in the ISO/SAE 21434.
III. Cybersecurity monitoring
Understand how cybersecurity monitoring is configured and learn what threat intelligence is and relevant best practices.
IV. Cybersecurity information
Learn which internal and external sources can provide cybersecurity information, prioritization criteria, and what are the benefits of a good cybersecurity monitoring infrastructure.
Know when cybersecurity triaging comes into play, what its role is, and what the process looks like in a visual overview. In this section, we will also go through an example of cybersecurity triaging.
VI. Introduction to cybersecurity event evaluation
Get introduced to cybersecurity event evaluation in the context of continual cybersecurity activities and how the ISO/SAE 21434 defines it.
VII. Cybersecurity event evaluation
Recognize what the goal of cybersecurity event evaluation is and discover which supporting documents are useful for event evaluation.
VIII. Sum up
To conclude this video course, we will provide you with a summary of the main lessons learned.